In May 2015 banyan published that they found over 30% of Official Images in Docker Hub Contain High Priority Security Vulnerabilities.
In December 2016 a major vulnerability CVE-2016-9962 (“on-entry vulnerability.”) was found in the Docker Engines which allowed local root users in a container to gain privileges by using ptrace to access file-descriptors of a process launched or moved into the container from another namespace.
At Red Hat we are continuously improving our view on security and introduced a new container scanning feature with CloudForms 4.2 and OpenShift 3.4 which allows CloudForms to flag an image in the docker registry after it found vulnerabilities and OpenShift will deny its execution next time someone will try to run that image.
CloudForms has multiple capabilities on how a docker scan can be initiated
-
- scheduled scan of the registry
- scan based on newly discovered images in the Registry
- manual execution of the scan via smart state analysis
Having this unique scanning feature with native integration in OpenShift is milestone in perspective of container security as you will have near real time monitoring of your images within the OpenShift environment.
This diagram is showing the flow as well as how we perform a scan on containers in the Red Hat OpenShift environment
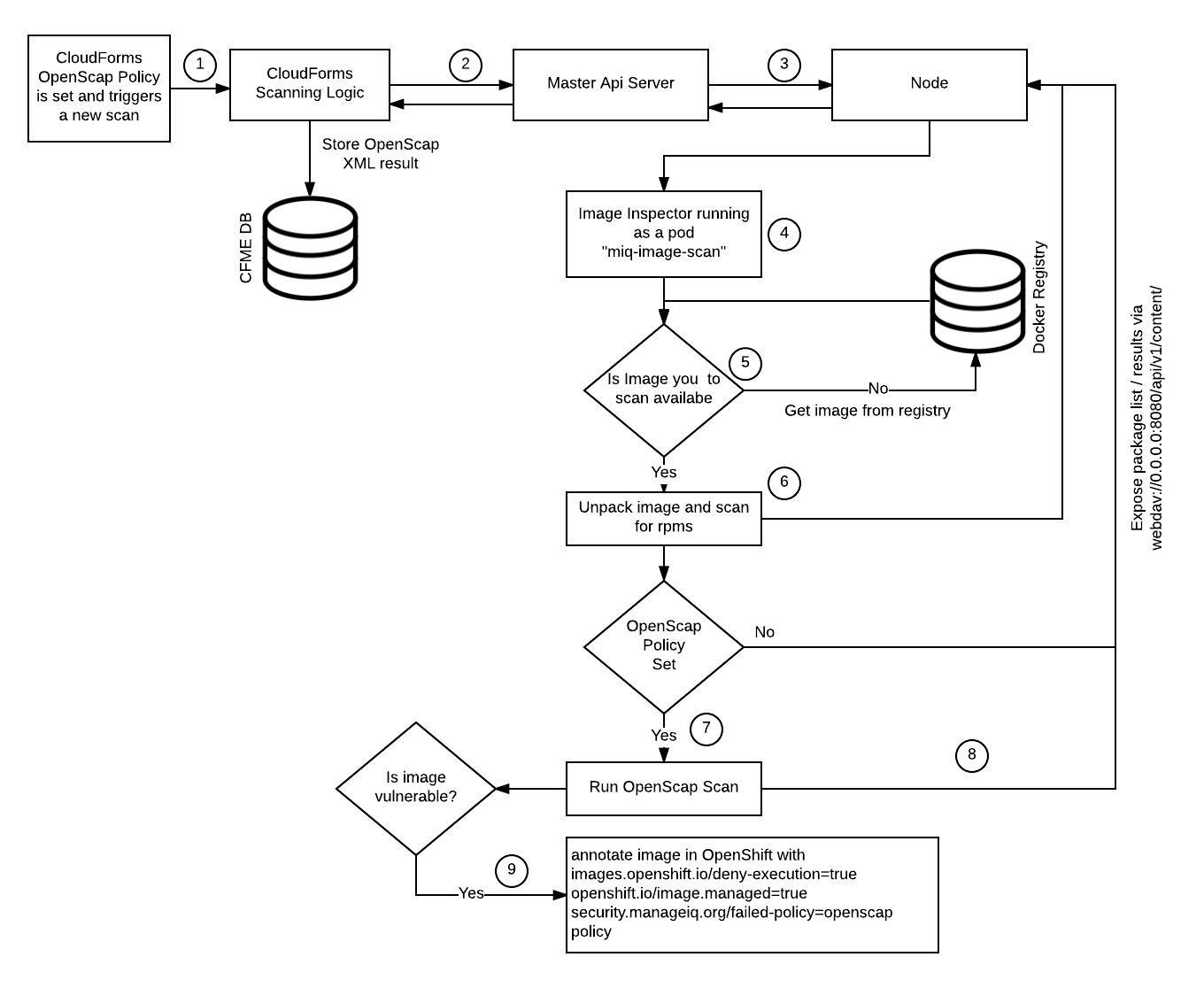
- CloudForms monitors the Openshift Provider and checks if it finds new images in the registry. If it finds a new image Cloudforms Triggers a scan
- CloudForms makes an encrypted call to OpenShift via bearer token (which was created during the initial configuration) and requests a manageiq-img-scan container to be scheduled in the management-infra project
- OpenShift schedules a new pod on an available node
- The manageiq-img-scan gets started
- The manageiq-img-scan scanner check if the image to scan is available in the registry and pull is down
- The image to scan is unpacked and its rpm content registered and sent to cloudforms
- As we enabled the OpenScap policy CloudForms also initiates the OpenScap scan
- After the OpenScap scan finishes the results get uploaded and a new report can be generated from the CloudForms UI
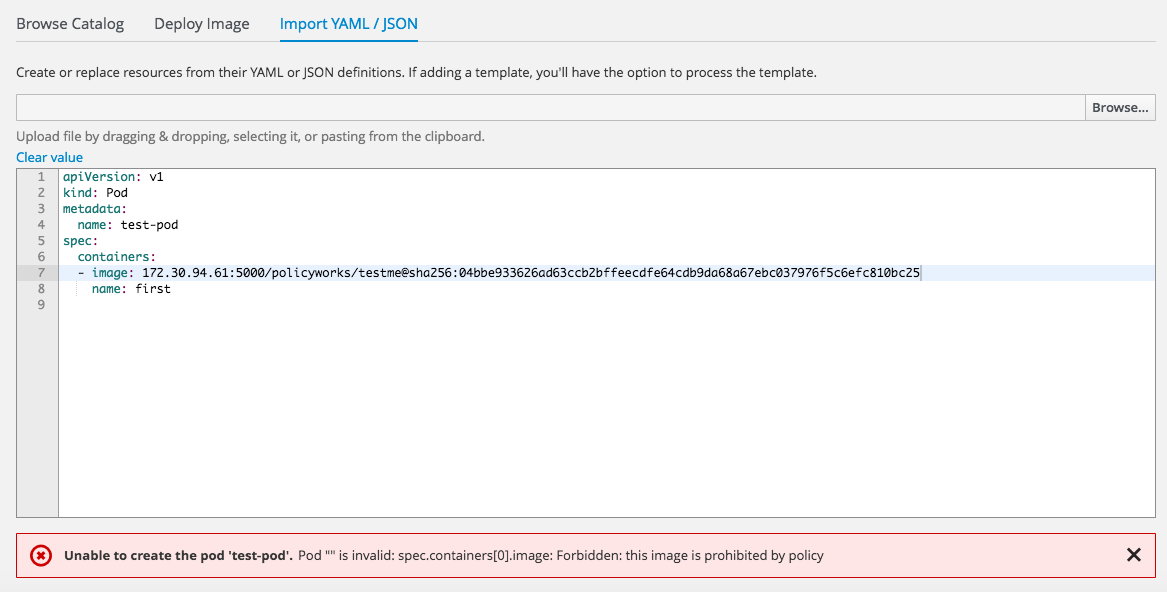
- If the scan found any vulnerabilities the CloudForms calls OpenShift to annotate the OpenShift image with images.openshift.io/deny-execution=true and prevents future images from running
The next time someone will try to start the vulnerable image OpenShift will alert the user that the image execution was blocked based on the policy annotation set by CloudForms.